Cryptocurrency Wallets Architecture: How Digital Asset Storage Works
Last month, I watched a seasoned DeFi developer lose $200,000 in a single transaction. Not from a smart contract exploit or oracle manipulation, but from a fundamental misunderstanding of how wallet architecture actually works. He assumed his hardware wallet was "storing" his tokens when it was merely protecting the keys that proved ownership. This distinction between key custody and asset storage represents one of the most critical yet misunderstood concepts in cryptocurrency development
The Architecture Misconception
Most engineers think of wallets as digital storage containers, similar to how we conceptualize traditional bank accounts. This mental model leads to dangerous assumptions in protocol design. In reality, cryptocurrencies exist only as entries in distributed ledgers. Your wallet doesn't contain Bitcoin or Ethereum—it contains cryptographic keys that prove you have the right to modify specific ledger entries.
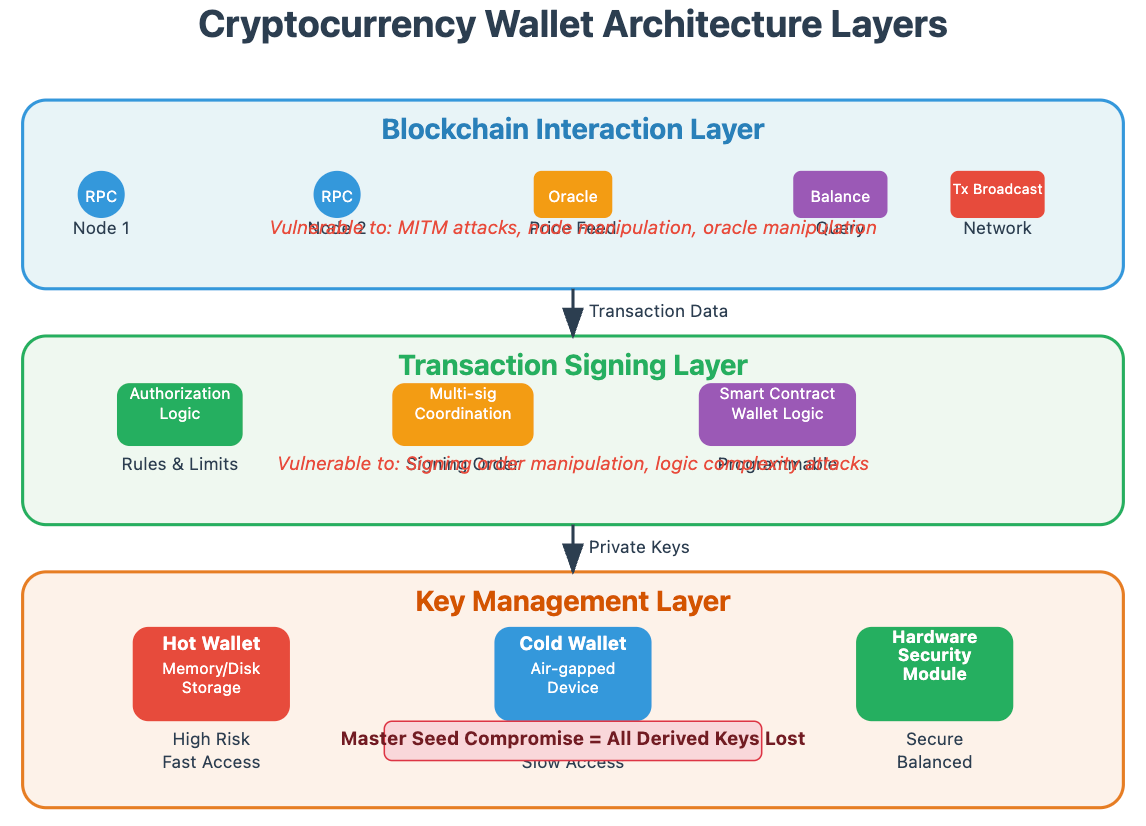
This architectural reality creates three distinct layers that every blockchain engineer must understand: the key management layer, the transaction signing layer, and the blockchain interaction layer. Each presents unique security challenges that can cascade into protocol-level vulnerabilities.
Key Management: The Foundation Layer
The key management layer determines how private keys are generated, stored, and accessed. Here's where most security failures originate. Hot wallets store keys in memory or on disk, creating attack vectors through memory dumps, file system access, or process injection. Cold wallets isolate keys on air-gapped devices, but introduce usability friction that often leads to implementation shortcuts.
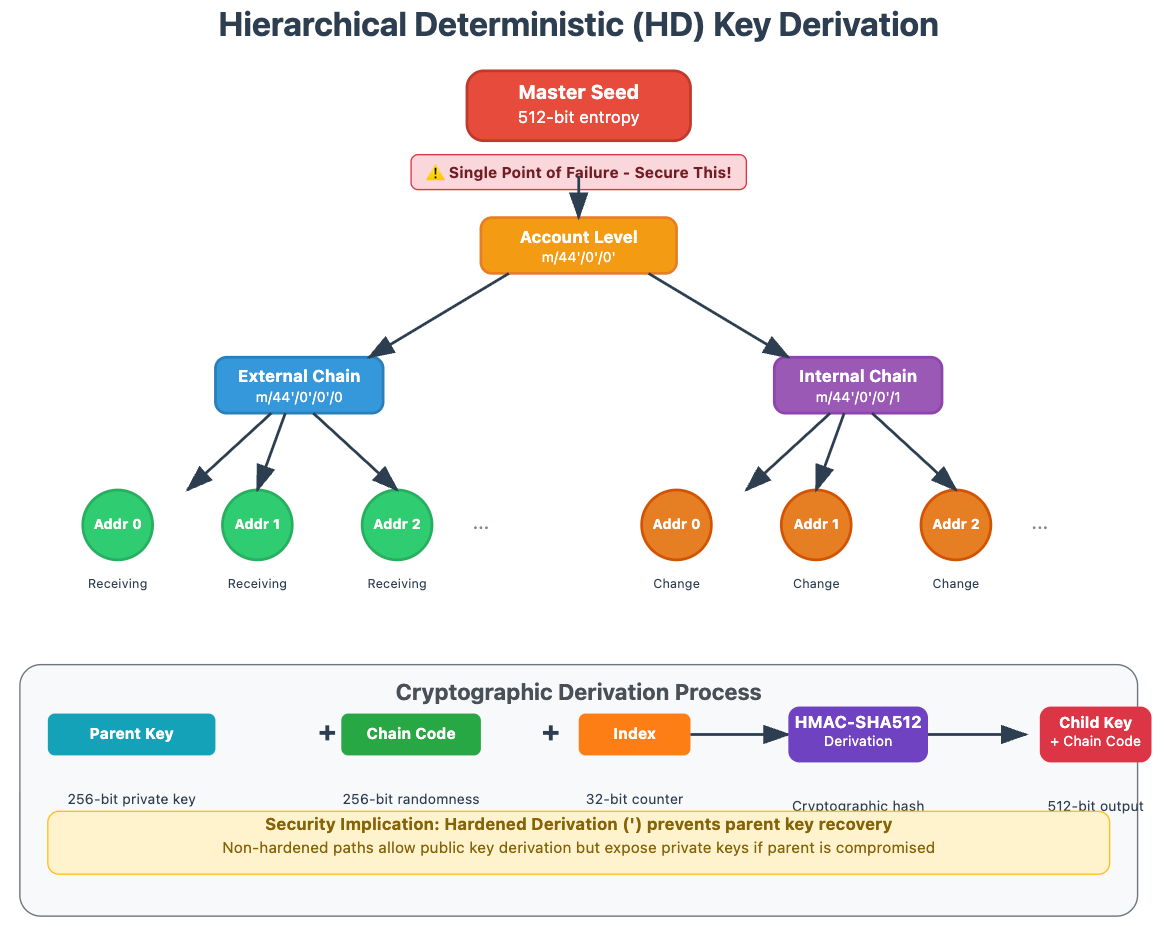
The critical insight most developers miss is that key derivation paths create hierarchical relationships between addresses. A compromised master seed doesn't just expose one address—it potentially exposes thousands of derived addresses following predictable patterns. This has profound implications for protocol design, especially for applications managing multiple user accounts or implementing account abstraction.
Transaction Signing: The Authorization Layer
The signing layer transforms transaction intentions into cryptographically verifiable proofs. This is where reentrancy-style attacks can occur at the wallet level. Multi-signature wallets, for instance, can be vulnerable to signing order manipulation where malicious actors trick legitimate signers into authorizing unintended transactions by presenting partial transaction data.
Smart contract wallets introduce additional complexity through their programmable logic. They can implement custom authorization rules, spending limits, and recovery mechanisms, but each feature expands the attack surface. The recent Argent wallet upgrades demonstrate how seemingly innocent feature additions can introduce new categories of vulnerabilities when the authorization logic becomes too complex.
Blockchain Interaction: The Communication Layer
The interaction layer handles communication with blockchain networks, including transaction broadcasting, balance queries, and state synchronization. This layer is particularly vulnerable to man-in-the-middle attacks and node manipulation. Many wallet implementations blindly trust RPC endpoints without verifying responses against multiple sources or implementing proper certificate pinning.
Oracle integration at this layer creates another attack vector. When wallets display token prices or portfolio values, they often rely on external price feeds that can be manipulated to trick users into making poor decisions. The principle of "verify don't trust" applies not just to smart contracts but to every external data source your wallet consumes.
Production Implementation Strategy
For immediate implementation, focus on these three architectural principles. First, implement deterministic key derivation with proper entropy sources and secure the master seed using hardware security modules or secure enclaves. Second, separate signing operations from network communication to prevent remote code execution attacks on your signing logic. Third, implement multi-source verification for all external data, including transaction broadcasting and balance queries.
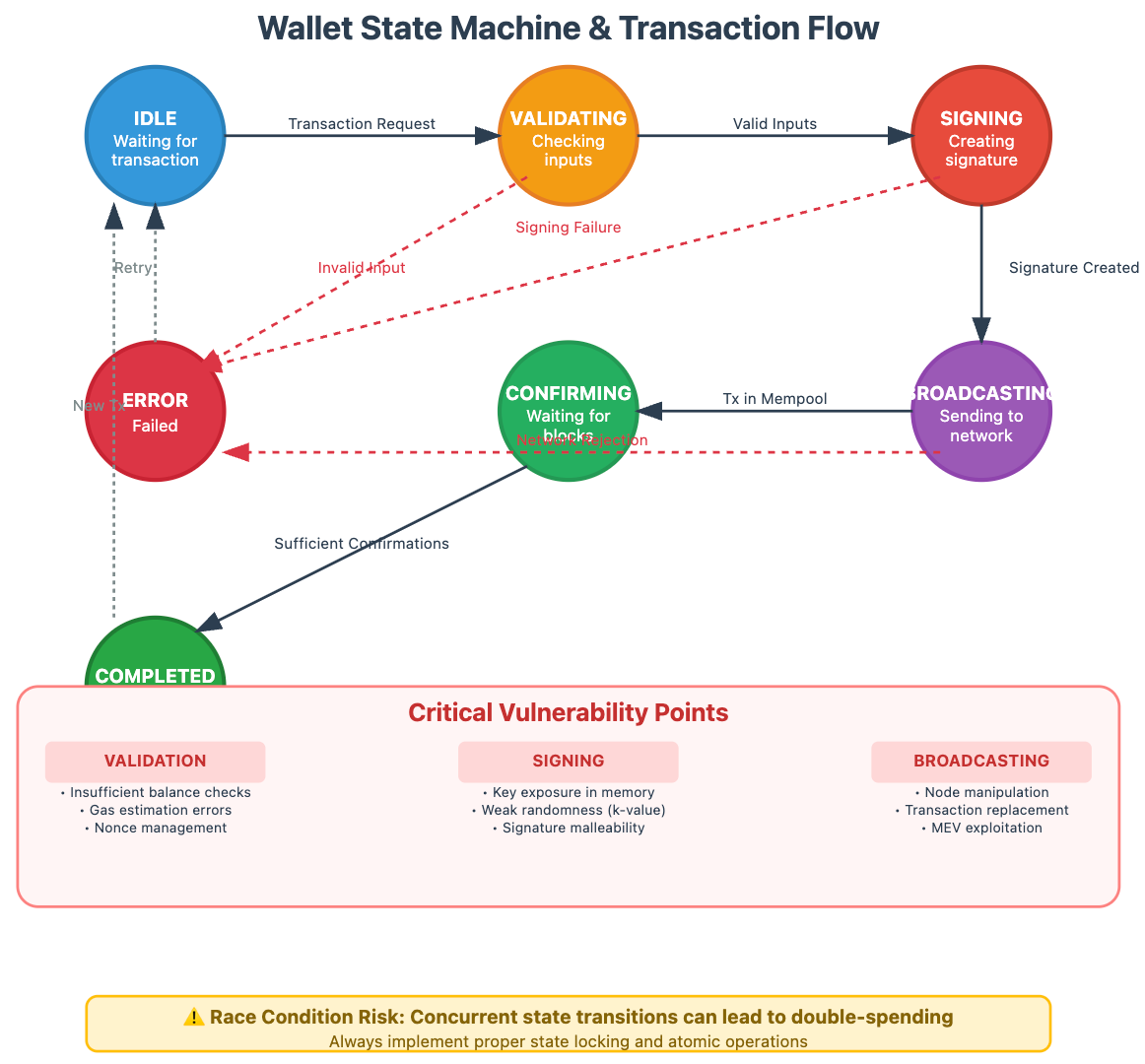
The most overlooked aspect is state synchronization resilience. When your wallet loses connectivity or encounters conflicting blockchain states, how does it recover? Build robust state reconciliation mechanisms that can handle network partitions, chain reorganizations, and inconsistent node responses without exposing users to double-spending or balance calculation errors.
Understanding these architectural layers transforms how you approach wallet integration in your protocols. Instead of treating wallets as black boxes, you can design interfaces that work with their security models rather than against them, creating more resilient and user-friendly decentralized applications.
// SPDX-License-Identifier: MIT
pragma solidity ^0.8.19;
import "@openzeppelin/contracts/security/ReentrancyGuard.sol";
import "@openzeppelin/contracts/access/AccessControl.sol";
import "@openzeppelin/contracts/security/Pausable.sol";
/**
* @title SecureSmartWallet
* @dev Production-ready smart contract wallet with comprehensive security measures
* @notice Implements multi-layer security including reentrancy protection,
* access controls, and oracle safety checks
*/
contract SecureSmartWallet is ReentrancyGuard, AccessControl, Pausable {
// Role definitions for granular access control
bytes32 public constant OWNER_ROLE = keccak256("OWNER_ROLE");
bytes32 public constant GUARDIAN_ROLE = keccak256("GUARDIAN_ROLE");
bytes32 public constant RECOVERY_ROLE = keccak256("RECOVERY_ROLE");
// State variables for security tracking
mapping(address => uint256) private _nonces;
mapping(bytes32 => bool) private _executedTransactions;
uint256 private _lastExecutionTime;
uint256 public constant MIN_EXECUTION_DELAY = 1 hours;
// Events for comprehensive logging
event TransactionExecuted(
address indexed to,
uint256 value,
bytes data,
uint256 nonce,
bytes32 txHash
);
event GuardianAdded(address indexed guardian);
event RecoveryInitiated(address indexed newOwner, uint256 timestamp);
// Custom errors for gas efficiency
error InvalidSignature();
error TransactionAlreadyExecuted();
error InsufficientBalance();
error ExecutionTooFrequent();
error UnauthorizedAccess();
modifier onlyOwnerOrGuardian() {
if (!hasRole(OWNER_ROLE, msg.sender) && !hasRole(GUARDIAN_ROLE, msg.sender)) {
revert UnauthorizedAccess();
}
_;
}
modifier rateLimited() {
if (block.timestamp < _lastExecutionTime + MIN_EXECUTION_DELAY) {
revert ExecutionTooFrequent();
}
_;
_lastExecutionTime = block.timestamp;
}
constructor(address owner, address[] memory guardians) {
// Initialize role-based access control
_grantRole(DEFAULT_ADMIN_ROLE, owner);
_grantRole(OWNER_ROLE, owner);
// Set up guardians for recovery scenarios
for (uint i = 0; i < guardians.length; i++) {
_grantRole(GUARDIAN_ROLE, guardians[i]);
emit GuardianAdded(guardians[i]);
}
}
/**
* @dev Secure withdrawal function with comprehensive protection
* @param to Recipient address
* @param amount Withdrawal amount
* @param nonce Unique transaction nonce to prevent replay
* @param signature Owner's signature for authorization
*/
function secureWithdraw(
address to,
uint256 amount,
uint256 nonce,
bytes calldata signature
)
external
nonReentrant
whenNotPaused
rateLimited
{
// Generate transaction hash for uniqueness check
bytes32 txHash = keccak256(
abi.encodePacked(
address(this),
to,
amount,
nonce,
block.chainid
)
);
// Prevent replay attacks
if (_executedTransactions[txHash]) {
revert TransactionAlreadyExecuted();
}
// Verify nonce progression (prevents out-of-order execution)
if (nonce != _nonces[msg.sender] + 1) {
revert InvalidSignature();
}
// Verify signature authenticity
address recovered = _recoverSigner(txHash, signature);
if (!hasRole(OWNER_ROLE, recovered)) {
revert InvalidSignature();
}
// Check-Effects-Interactions pattern for reentrancy protection
// CHECKS: Validate all conditions first
if (address(this).balance < amount) {
revert InsufficientBalance();
}
// EFFECTS: Update state before external calls
_executedTransactions[txHash] = true;
_nonces[msg.sender] = nonce;
// INTERACTIONS: External calls last
(bool success, ) = to.call{value: amount}("");
require(success, "Transfer failed");
emit TransactionExecuted(to, amount, "", nonce, txHash);
}
/**
* @dev Execute arbitrary contract calls with security checks
* @param to Target contract address
* @param value ETH value to send
* @param data Contract call data
* @param nonce Unique transaction nonce
* @param signature Owner's signature
*/
function executeTransaction(
address to,
uint256 value,
bytes calldata data,
uint256 nonce,
bytes calldata signature
)
external
nonReentrant
whenNotPaused
onlyOwnerOrGuardian
{
bytes32 txHash = keccak256(
abi.encodePacked(
address(this),
to,
value,
data,
nonce,
block.chainid
)
);
if (_executedTransactions[txHash]) {
revert TransactionAlreadyExecuted();
}
// Additional security: Prevent self-destruct calls
require(
!_isSelfDestructCall(data),
"Self-destruct calls prohibited"
);
address recovered = _recoverSigner(txHash, signature);
if (!hasRole(OWNER_ROLE, recovered) && !hasRole(GUARDIAN_ROLE, recovered)) {
revert InvalidSignature();
}
_executedTransactions[txHash] = true;
_nonces[recovered] = nonce;
(bool success, bytes memory returnData) = to.call{value: value}(data);
if (!success) {
// Bubble up the revert reason
assembly {
revert(add(returnData, 32), mload(returnData))
}
}
emit TransactionExecuted(to, value, data, nonce, txHash);
}
/**
* @dev Multi-signature recovery mechanism for lost keys
* @param newOwner New owner address to set
* @param guardianSignatures Array of guardian signatures
*/
function initiateRecovery(
address newOwner,
bytes[] calldata guardianSignatures
) external {
require(guardianSignatures.length >= 2, "Insufficient guardian signatures");
bytes32 recoveryHash = keccak256(
abi.encodePacked(
"RECOVERY",
newOwner,
block.timestamp,
block.chainid
)
);
// Verify guardian signatures
address[] memory signers = new address[](guardianSignatures.length);
for (uint i = 0; i < guardianSignatures.length; i++) {
address signer = _recoverSigner(recoveryHash, guardianSignatures[i]);
require(hasRole(GUARDIAN_ROLE, signer), "Invalid guardian signature");
// Prevent signature reuse
for (uint j = 0; j < i; j++) {
require(signers[j] != signer, "Duplicate guardian signature");
}
signers[i] = signer;
}
// Transfer ownership
_revokeRole(OWNER_ROLE, getRoleMember(OWNER_ROLE, 0));
_grantRole(OWNER_ROLE, newOwner);
emit RecoveryInitiated(newOwner, block.timestamp);
}
/**
* @dev Emergency pause function for security incidents
*/
function emergencyPause() external onlyOwnerOrGuardian {
_pause();
}
function emergencyUnpause() external {
require(hasRole(OWNER_ROLE, msg.sender), "Only owner can unpause");
_unpause();
}
// Internal helper functions
function _recoverSigner(
bytes32 hash,
bytes memory signature
) internal pure returns (address) {
bytes32 ethSignedMessageHash = keccak256(
abi.encodePacked("\x19Ethereum Signed Message:\n32", hash)
);
(bytes32 r, bytes32 s, uint8 v) = _splitSignature(signature);
return ecrecover(ethSignedMessageHash, v, r, s);
}
function _splitSignature(bytes memory sig)
internal
pure
returns (bytes32 r, bytes32 s, uint8 v)
{
require(sig.length == 65, "Invalid signature length");
assembly {
r := mload(add(sig, 32))
s := mload(add(sig, 64))
v := byte(0, mload(add(sig, 96)))
}
// Ensure canonical signature format
if (v < 27) {
v += 27;
}
require(v == 27 || v == 28, "Invalid signature v value");
}
function _isSelfDestructCall(bytes calldata data)
internal
pure
returns (bool)
{
if (data.length < 4) return false;
// Check for selfdestruct function selector
bytes4 selector = bytes4(data[:4]);
return selector == 0xff; // selfdestruct opcode
}
// View functions
function getNonce(address user) external view returns (uint256) {
return _nonces[user];
}
function isTransactionExecuted(bytes32 txHash)
external
view
returns (bool)
{
return _executedTransactions[txHash];
}
receive() external payable {}
}