Bitcoin Technology Simplified: How Cryptocurrency Actually Works
Newsletter #5 in our "Cryptocurrency and Bitcoin" series
Ever wondered what's really happening when you send bitcoin to someone? Today we'll demystify the core technology that powers Bitcoin, breaking down the complex mechanisms into digestible concepts that will give you a solid foundation for understanding cryptocurrency.
The Essence of Bitcoin
At its heart, Bitcoin is a decentralized ledger that records every transaction ever made in its network. Unlike traditional banking systems where a central authority (like a bank) maintains the ledger, Bitcoin's ledger—called the blockchain—is distributed across thousands of computers worldwide.
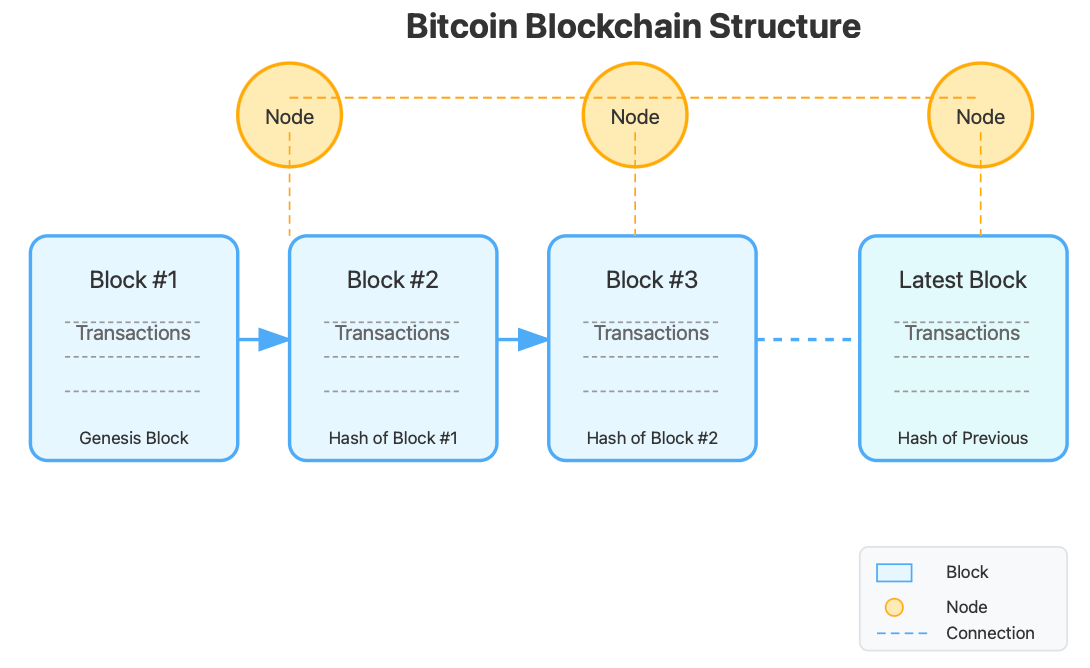
Bitcoin Blockchain Visualization
The Three Key Components
Bitcoin's technology rests on three fundamental pillars:
Blockchain: The distributed ledger that records all transactions
Mining: The process that secures the network and validates transactions
Cryptography: The mathematical security layer that ensures trust without central authority
Let's explore each in depth.
Blockchain: The Digital Ledger
The blockchain is essentially a chain of blocks, where each block contains:
A batch of verified transactions
A timestamp
A reference to the previous block (called a hash)
This structure creates an immutable record—once a block is added, it cannot be altered without changing all subsequent blocks, which would require enormous computational power.
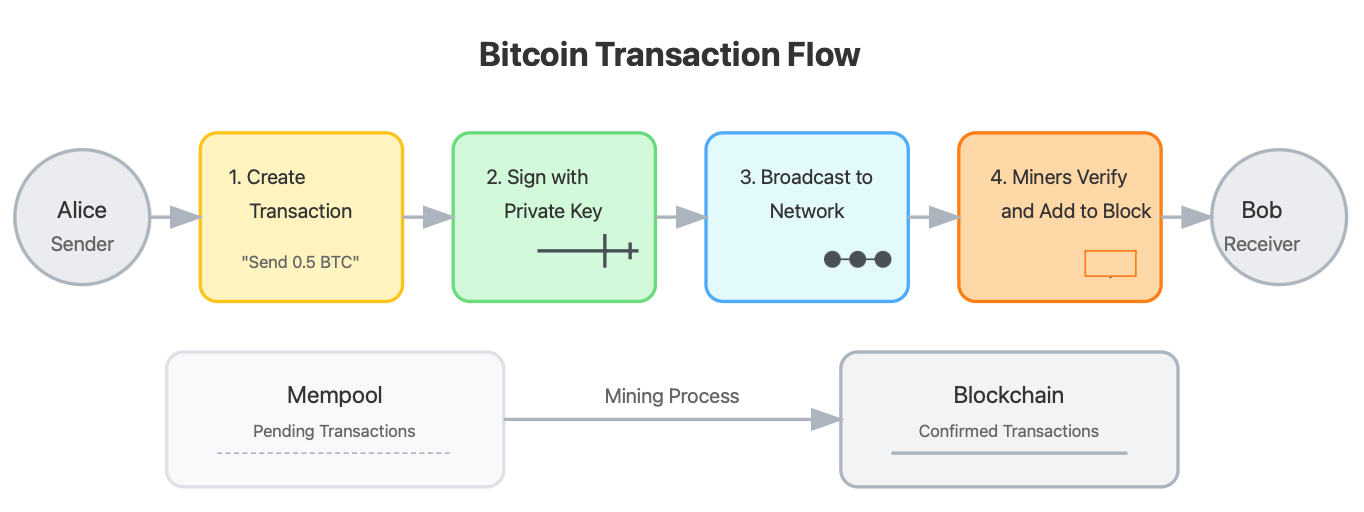
Bitcoin Transaction Flow
Anatomy of a Bitcoin Transaction
When you send bitcoin, here's what actually happens:
Transaction Creation: You specify the recipient's address and the amount to send
Digital Signing: Your wallet creates a digital signature using your private key
Broadcasting: Your transaction is broadcast to the entire Bitcoin network
Mempool Collection: Miners collect your transaction in their "mempool" (memory pool)
Verification: Miners verify your transaction by confirming you have the funds and your signature is valid
Block Addition: Your transaction is added to a block with other verified transactions
Mining: The block is "mined" through a computational process
Confirmation: Once mined, your transaction is considered confirmed
The Mining Process: Securing the Network
Mining serves two critical functions: it adds new blocks to the blockchain and issues new bitcoins according to a predetermined schedule.
Bitcoin Mining and Proof of Work
Proof of Work Explained
Bitcoin uses a consensus mechanism called "Proof of Work" (PoW). Here's how it works:
The Mining Puzzle: Miners compete to solve a complex mathematical puzzle
Finding the Nonce: They try to find a special number (nonce) that, when combined with the block data and hashed, produces a hash with a specific pattern (usually starting with a certain number of zeros)
Computational Challenge: The only way to solve this puzzle is through trial and error, requiring significant computational power
Reward: The first miner to solve the puzzle gets to add the block to the blockchain and receives a reward in newly created bitcoins (currently 3.125 BTC per block) plus transaction fees
The difficulty of this puzzle automatically adjusts every 2016 blocks (approximately two weeks) to maintain a consistent block creation rate of about one block every
Proof of Work Continued
The difficulty of mining adjusts every 2016 blocks (approximately two weeks) to maintain a consistent block creation rate of about one block every 10 minutes. This self-regulating system ensures that:
As more miners join, the difficulty increases
As miners leave, the difficulty decreases
The supply of new bitcoins remains predictable and controlled
This process creates what economists call "artificial scarcity," giving Bitcoin its value proposition as "digital gold."
The Cryptography Behind Bitcoin
Cryptography forms the security backbone of Bitcoin, providing trust without requiring centralized authority.
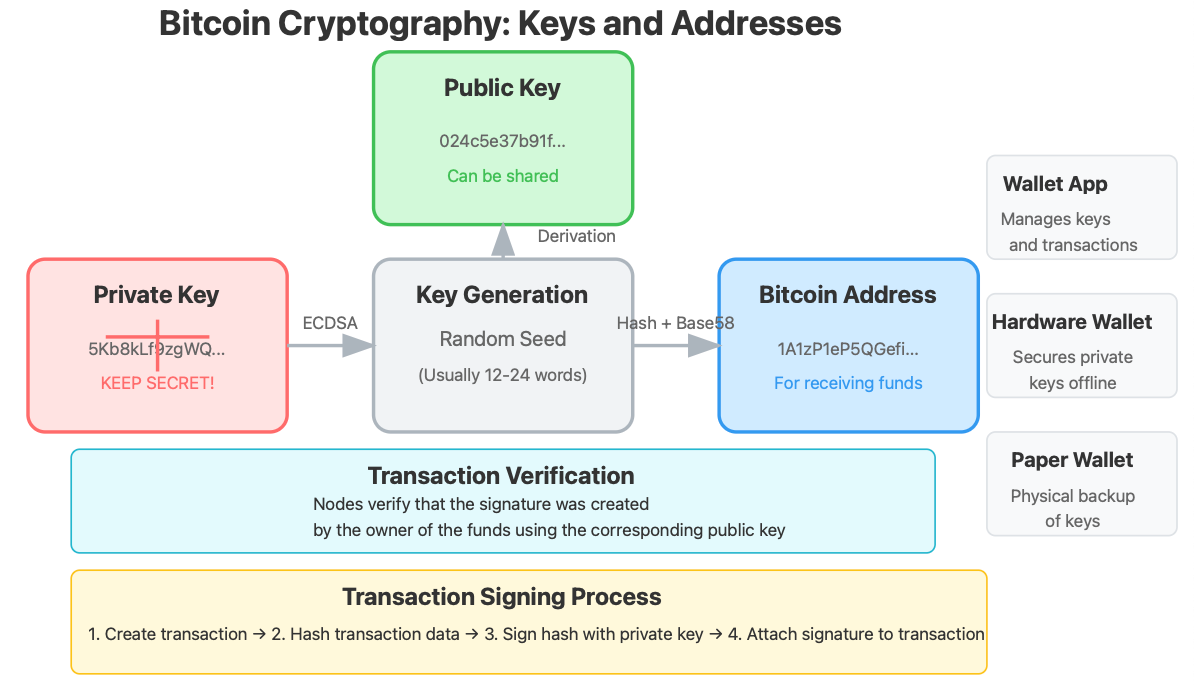
Bitcoin Cryptography and Keys
Public and Private Keys
Bitcoin uses asymmetric cryptography, which involves two types of keys:
Private Key: A secret number known only to you that acts as your digital signature
Must be kept absolutely secure
Losing your private key means permanently losing access to your bitcoin
Usually represented as a 12-24 word "seed phrase" in modern wallets
Public Key: Derived from your private key using Elliptic Curve Digital Signature Algorithm (ECDSA)
Can be shared with others
Used to verify signatures but cannot be used to derive your private key
Bitcoin Address: A hashed version of your public key
What others see when you receive bitcoin
Example: 1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa
When you "send" bitcoin, you're actually creating a digital message (transaction) that is signed with your private key. Any node in the network can verify this signature using your public key, proving you authorized the transaction without revealing your private key.
Wallets: Managing Your Bitcoin
Despite the name, bitcoin wallets don't actually "store" your coins. They store your keys and provide an interface to interact with the blockchain.
Types of Wallets:
Software Wallets
Mobile apps (e.g., BlueWallet, Muun)
Desktop software (e.g., Electrum, Bitcoin Core)
Web-based (e.g., Blockchain.com)
Hardware Wallets
Physical devices that store keys offline (e.g., Ledger, Trezor)
Considered the most secure option for significant holdings
Paper Wallets
Physical copies of your keys
Completely offline but vulnerable to physical damage
Real-World Use Cases
1. International Remittances
Maria in the United States wants to send money to her family in El Salvador, where Bitcoin is legal tender. Traditional wire transfers would cost 5-7% and take days. With Bitcoin, she pays less than $1 in fees, and the transfer completes in under an hour.
2. Store of Value
Alex is concerned about inflation eroding his savings. He allocates 5% of his portfolio to Bitcoin as a hedge against monetary debasement, similar to how others might invest in gold.
3. Micropayments
A content creator enables Bitcoin micropayments through the Lightning Network (a layer-2 solution built on top of Bitcoin), allowing fans to support their work with payments as small as a few cents—transactions that would be impractical with traditional payment systems.
Common Misconceptions
"Bitcoin is anonymous": Bitcoin is pseudonymous, not anonymous. All transactions are publicly recorded on the blockchain, though they're linked to addresses rather than personal identities.
"Bitcoin can be hacked": While individual exchanges or wallets can be compromised, the Bitcoin protocol itself has never been hacked. Its security comes from its decentralized nature and cryptographic underpinnings.
"Bitcoin has no intrinsic value": Bitcoin's value derives from its utility as a permissionless, censorship-resistant payment network and its scarcity (only 21 million will ever exist).
Looking Forward
Bitcoin continues to evolve through soft forks (backward-compatible upgrades) and layer-2 solutions like the Lightning Network. These improvements aim to address scalability challenges while maintaining the core principles of decentralization and security that have made Bitcoin revolutionary.
Understanding the fundamental technology behind Bitcoin helps demystify what often seems like complex financial magic. At its core, Bitcoin is simply a creative combination of existing technologies—cryptography, peer-to-peer networking, and consensus mechanisms—arranged in a way that creates a system with remarkable properties: permissionless, borderless, censorship-resistant money.
In our next newsletter, we'll explore the Lightning Network and how it's addressing Bitcoin's scalability challenges to enable faster, cheaper transactions while preserving security.
If you found this article helpful, please share it with friends interested in understanding cryptocurrency fundamentals. Questions or topic suggestions for future newsletters? Reply to this email—I'd love to hear from you!